http://www.mesa-sys.com/~eternal/mexcrk1.zip - (116k).
Welcome once again to a new section. Just a word to the confused amongst you, essentially a CrackMe is a program written for the express purpose of reversing. CrackMe's vary in difficulty a great deal but if you have the time you should study them and adapt your reversing techniques to beat them.
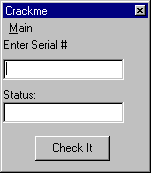
I'll start by just examining this example from MEXELiTE, its a very simple scheme best accomplished using SoftICE (using the disassembler will teach you very little). So launch the program, here's the screen you should be looking at:

So lets enter a fake number in the top dialog, you'll find a >bpx Hmemcpy works well in SoftICE, now just start tracing to this code, (use either F10 or F12), once again watch the pattern, user into kernel32 then into our program with some stack heavy code until we reach this:
:0042D534 MOV EAX,[EBP-04] <-- EAX holds code entered.
:0042D537 MOV EDX,0042D590 <-- EDX holds string Benadryl.
:0042D53C CALL 004038D0 <-- Compare.
:0042D541 JZ 0042D555 <-- Jump_good_code.
In code terms there's little to learn here, and under the inspection of W32Dasm you would have found this code very easily. However, this simple CrackMe uses code which you will see a lot of in many shareware programs.