http://www.siliconpixels.com
FTP Search: Cpix10.exe (6.04Mb)
For really new reversers Visual Basic programs can sometimes be a sticking point, the main reason of course is that most "newbies" when starting out use tutorials which use StringRef's to locate the protection. At the time I was writing this no tools would neatly add VB StringRef's to your desired environment, this however has changed, patch W32Dasm 8.93 according to my instructions in Septembers news column.
We'll launch the program and select "Settings", "Register" and fill in our name and serial # (notice how a string of length 14 fits neatly in the input box). The error appears, now we know VB uses wide-char strings, so lets just make a note of the error message :-
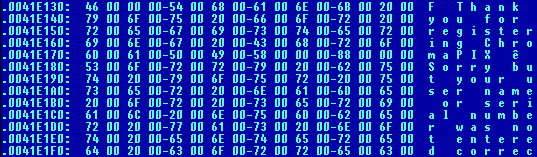
Sorry but your username or serial number was not entered correctly 53 00 6F 00 72 00 72 ...Using your favourite HEX editor (need I recommend Hiew), we search for this sequence in cpix.exe :-

At .0041E180 we have our error text, lets use this by switching to our disassembly listing, searching for 0041E180 (we find just 1 occurence) :-
:0051E1D7 MOV DWORD PTR [EBP+FFFFFF34], 0041E180 <-- soon to be pushed. :0051E20F CALL MSVBVM50.rtcMsgBox <-- for this message box. :0051E0AC TEST SI, SI <-- good_or_bad_flag. :0051E0D3 JZ 0051E1CB <-- beggar_off_bad_serial_#_jump. :0051E0E5 MOV DWORD PTR [EBP+FFFFFF34], 0041E134 <-- and the good guy. :0051E11D CALL MSVBVM50.rtcMsgBox <-- gets this message box.We could now attempt to trace the first 2 lines of code upwards, but VB programs are notorious for inefficient code and the deciding check might well be some distance away, we can however pinpoint it more quickly by searching for 0041E134 (the location of the "Thanks for registering ChromaPIX" message (code shown above)), and within 5 minutes we know exactly where we want to bpx for.
Interestingly locating a good code isn't actually as easy as it might look, before the deciding check we see a call to __vbaStrCmp, but this isn't what you might think, recall we are interested in SI and not EAX which is where __vbaStrCmp returns its result. The deciding CALL is sub_00506FD0 and this I should add is not a short function. Naturally I'll discuss only the highlights (if you want to avoid a long trace you can safely bpx for 00508332).
The first 2 interesting things to note are the programs encryption of specific strings, in particular you can observe the decryption of "s o f u n n y t o c r a c k" and "T R P S 1 9 9 8", both are evidently disliked by the program as names (the first is perhaps more of a taunt, the second is a warez group perhaps responsible for cracking previous versions, which had a different scheme anyhow). At 00508332 we reach our first check, the first 4 positions of a valid serial # must be 'SPC0'.
Further checks include the 10th position needing to be a hyphen '-', a good code must have length 0xE (005083AC) and a valid name a minimum of length 12 decimal (00508436). In fact a valid name must also have a minimum of 2 space characters as these will be counted in the loop ending at 0050852C and you will be fired to the bad guy code if there are less or given an error if you force the code.
The algorithm is found below CALL 004149AC which is actually a neat JMP to the protection spdsp220.dll. All you literally need to do is rip this code directly from SoftICE as the program uses __vbaStrToAnsi to convert the wide-char name just before. The length is padded to 32 decimal with 0x20 bytes. You'll find my ASM key generator here (coded without any error checking in under 3 minutes), the return value in EAX has 3 added too it and this forms the 5 digit number (positions 5 onwards). The last 4 positions can be any numbers you desire.
This scheme isn't bad but I'm curious why the protector chose to use his own function (crc16) inside a separate dll to do the work, I reckon its actually because the programmer came from a C++ background and reckoned on VB as being the best tool to create just the user-interface (a case of old habits dying hard perhaps). Needless to say my standard comment applies wrt using this software without paying the $120 registration fee.
 Back to Main Index,
Visual Basic.
Back to Main Index,
Visual Basic.