Let's start our cracking
session by looking at the NAG-Screen that will be displayed if you're in the trial period
(I've executed ViaVoice already once):
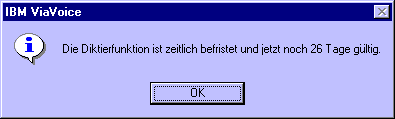
If you can't understand
german, the following translation is for you: "The dictate function is time limited
and 26 days valid from now on." So IBM gave us the information on the protections
(maybe they want to see if anyone can Reverse Engineer ViaVoice): Time Limited & NAG
Screen. I hate clicking OK-Buttons to start a program, so let's crack the Trial-NAG first.
What do you think this NAG-Screen looks like? - At least I think it's looking like
a standard-message-box. In this case MessageBox[A] would work (as you may read in the cRACKER's n0TES' Window-Generating-Part). So set a BPX
to MessageBoxA and restart ViaVoice. After you've pressed F11 and then pressed the
OK-Button, SoftICE will display the information, that you're debugging VVLUM.DLL - and
you'll get the something like the following code snippet:
:00CA1C2A 85C0 TEST EAX,EAX
:00CA1C2C 752A JNZ 00CA1C58
:00CA1C2E 52 PUSH EDX
:00CA1C2F 8D8C2470020000 LEA ECX,[ESP+00000270]
:00CA1C36 68481ACB00 PUSH 00CB1A48
:00CA1C3B 51 PUSH ECX
:00CA1C3C FFD3 CALL EBX
:00CA1C3E 83C40C ADD ESP,0C
:00CA1C41 8D94246C020000 LEA EDX,[ESP+0000026C]
:00CA1C48 6A40 PUSH 40
:00CA1C4A 685815CB00 PUSH 00CB1558
:00CA1C4F 52 PUSH EDX
:00CA1C50 6A00 PUSH 00
:00CA1C52 FF15E032CB00 CALL [USER32!MessageBoxA]
:00CA1C58 8B442414 MOV EAX,[ESP+14]
:00CA1C5C 85C0 TEST EAX,EAX
:00CA1C5E 740A JZ 00CA1C6A
:00CA1C60 50 PUSH EAX
:00CA1C61 FF15C832CB00 CALL [00CB32C8]
:00CA1C67 83C404 ADD ESP,04
:00CA1C6A 8B442410 MOV EAX,[ESP+10]
:00CA1C6E 5F POP EDI
:00CA1C6F 5E POP ESI
:00CA1C70 5D POP EBP
:00CA1C71 5B POP EBX
:00CA1C72 81C45C030000 ADD ESP,0000035C
:00CA1C78 C3 RET |
So what can we do to get rid of that damn NAG now? - Well, we could NOP out the CALL
MessageBoxA for instance - but it's better to change as less as possible. Look at the code
snippet again!
Why not change that JNZ at CA1C2A to a JMP? It should work, since no flags, etc.
are set. Now exit ViaVoice and disable your MessageBoxA-breakpoint. Copy the VVLUM.DLL to VVLUM.OLD and HexEdit VVLUM.DLL using Hacker's View. Now
search for
85C0752A
and replace it with
85C0EB2A
Ok - there won't be a NAG if we're in the
trial period. Now we have to remove ViaVoice's real protection: the time limit. So set
your system clock at least 3 months ahead and start ViaVoice. Then the following
dialogbox get's displayed:
If you can't understand
german, the following translation is for you: "Your '60 day dictate function' license
has expired. We hope ...". Since we know that a standard message-box is displayed, we
can enable our MessageBoxA breakpoint and restart ViaVoice.
After you've pressed F11 and then pressed the "OK" button, SoftICE will
display something like the following code snippet:
:00CA1063 6A40 PUSH 40
:00CA1065 685815CB00 PUSH 00CB1558
:00CA106A 3D00000010 CMP EAX,10000000
:00CA106F 687011CB00 PUSH 00CB1170
:00CA1074 6A00 PUSH 00
:00CA1076 750D JNZ 00CA1085
:00CA1078 FF15E032CB00 CALL [USER32!MessageBoxA]
:00CA107E 66B80B00 MOV AX,000B
:00CA1082 5F POP EDI
:00CA1083 5E POP ESI
:00CA1084 C3 RET
:00CA1085 FF15E032CB00 CALL [USER32!MessageBoxA]
:00CA108B 5F POP EDI
:00CA108C 66B80C00 MOV AX,000C
:00CA1090 5E POP ESI
:00CA1091 C3 RET |
We must execute the RET
instruction to get something more interesting. So do this now. SoftICE will now display
something like the following code snippet, which is no longer in VVLUM.DLL - now the code
snippet is located in SPENGIO.DLL:
:004BEFCD FF157CA74D00 CALL [KERNEL32!GetProcAddress]
:004BEFD3 85C0 TEST EAX,EAX
:004BEFD5 7419 JZ 004BEFF0
:004BEFD7 8B8C2420010000 MOV ECX,[ESP+00000120]
:004BEFDE 51 PUSH ECX
:004BEFDF 53 PUSH EBX
:004BEFE0 FFD0 CALL EAX
:004BEFE2 83C408 ADD ESP,08
:004BEFE5 663D0A00 CMP AX,000A
:004BEFE9 7505 JNZ 004BEFF0
:004BEFEB BD01000000 MOV EBP,00000001
:004BEFF0 8BC5 MOV EAX,EBP
:004BEFF2 5D POP EBP
:004BEFF3 5F POP EDI
:004BEFF4 5E POP ESI
:004BEFF5 5B POP EBX
:004BEFF6 81C404010000 ADD ESP,00000104
:004BEFFC C3 RET |
At 4BEFE5 AX is checked
against 0A. As you may think then a flag will be set - which is the case at 4BEFEB. This flag will then be tested. So if you have another
look at the following code snippet from VVLUM.DLL, you can check your thoughts:
:00CA104C E84F000000
CALL 00CA10A0
:00CA1051 8B442420
MOV EAX,[ESP+20]
:00CA1055 83C414
ADD
ESP,14
:00CA1058 85C0
TEST EAX,EAX
:00CA105A 7507
JNZ 00CA1063
:00CA105C 66B80A00 MOV
AX,000A
:00CA1060 5F POP
EDI
:00CA1061 5E POP
ESI
:00CA1062 C3 RET |
The MOV AX,000A instruction
at CA105C is just executed if you are in the trial period - if you're not in the trial
period, the JNZ instruction at CA105A will be executed, which sets AX either to 0B or 0C. So the CMP AX,00A instruction at
4BEFE5 from SPENGIO.DLL is the time limit check.
So to crack the time limit, we must replace the JNZ CA1063 instruction at CA105A
with two NOPs (or something like INC EAX & DEC EAX). So HexEdit VVLUM.DLL using
Hacker's View. Now search for
1485C07507
and replace it with
1485C09090
Then we'll pass the CMP AX,00A instruction at
4BEFE5 from SPENGIO.DLL and ViaVoice will never expire. Now IBM should know, that it's
possible & quite easy to Reverse Engineer ViaVoice. Do you have any questions? |