Cracking Tutorial for Quick Heal 3.14 |
||||||||||||||
| Before we start, please read the Disclaimer section of this essay! | ||||||||||||||
|
||||||||||||||
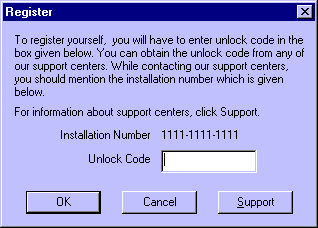
First of all, start Quick
Heal. The first thing I noticed was the info of the "Installation Number", which
is partly calculated from your Win 95/98 Reg-#. The installation number looks like the following:
NNNN-NNNN-NNNN and is stored in your registry. If you want to register the program a
dialog box asking for an unlock code will be displayed (I've changed the Installation
Number of course):
Since we want to get a valid
Unlock Code for our Installation Number, we enter any number - like 111111111111.
Then we enter SoftICE by pressing CTRL-D to set the necessary breakpoints. For this
program we can use GetDlgItemTextA as our BPX. So set a BPX to GetDlgItemTextA and return
to Quick Heal. Now press the "OK"-Button. SoftICE will pop-up at the
GetDlgItemTextA-Function. Now press F11 to return to the function that called
GetDlgItemTextA. You'll see the following code:
So after we've returned from the GetDlgItemTextA function (F11), we'll step through the code using the F10-key. We'll jump to 41F1A7. The code at 41F1A7 will look like the following:
Now step forward through the code. Afer you've passed the "RET 00C"-instruction, you'll get the following code:
At 40A2F3 type D EAX to see what's in EAX. Then step over the call (F10). Hey, what's that? EAX has changed it's value to our Installation Number 1111-1111-1111. Ok now at 40A302 look at the value of EAX again. Now EAX contains our enterd Unlock Code and our Installation Number. If you have a look at ECX, you'll find out that it contains our Installation Number. Since there is a "CMP EAX,1"-instruction (check if Unlock-Code is valid) after the "CALL 4064BA", we have to enter this call by pressing F8; if we want to patch Quick Heal 3.14, we would have NOPed out the JNE-instruction. In Quick Heal it would work - but we want to find our Unlock Code. Inside the CALL to 4064BA, you'll find the following code:
At 4064D1 ESI contains our Installation Number. Step over the CALL 0040C040 by pressing F10. You'll see the following code:
At 4064E2, EDI contains the H-part of the following part of our Installation Number: NNNN-HHNN-NNNN. EAX contains the G-part of the following part of our Installation Number: NNNN-GGGG-GGGG (inclusive the dash). Since we know this, we can trace forward through the following code:
As you already know, we can change the Installation Number, which is stored in the registry. The coders from Quick Heal, probably know that a cracker will 'try' to do this and so the check if the Installation Number is valid or if it's invalid. This is done in the CALL 40CA50. The call 40CA50 will use "NOT ECX" (which means, ECX = -1) and "MOV EAX,ECX" if your Installation Number is invalid. So the check at 4064EE will be failed - and you won't jump to 4064F6 - and EAX will then be XORed (4064F2) and then the check at 40A30C will be failed, because when you XOR EAX,EAX then EAX is 0 - and not the needed 1 to pass the test at 40A30C. So if your Installation Number is valid, you'll see the following code:
At, 4064F9 EAX will contain the H-part of the following part of our Installation Number: NNNN-HHNN-NNNN. And at 4064FA, ESI will contain our complete Installation Number. Now step over the CALL by pressing F10 and you'll see the following code:
At 406505, EDI contains the G-part of the following Installation Number: NNNN-GGGG-GGGG (inclusive the dash). Then there's a (not important) CALL. EAX contains at 40650E the L-part of the following Installation Number: NNNN-NNNN-LLLL (inclusive the dash before the first L). Since the dash is unimportant, it is removed by the "INC EAX"-instruction at 40650E. ECX contains at 406512 the L-part of our Installation Number (without the dash). Then it is checked (in the CALL) if EAX and ECX are different. If they are different, the call 40CA50 will use "NOT ECX" (which means, ECX = -1) and "MOV EAX,ECX" - and then you'll fail the check at 40651E. If they aren't different, Quick Heal will continue checking you Unlock Code against the real Unlock Code. So you'll see the following code:
At 40652B, ESI will be the complete Installation Number.
At 406537, EAX will be the real Unlock Code. It looks like NNNN-NNNNNNNN. Write this code down. If you do a D EBP+0C you'll see the Unlock Code you've enterd. So simply press CTRL-D to return to Quick Heal. Now enter the unlock code you've written down. The Unlock Code for the Installation Number 1111-1111-1111 is 3333-11119999. Now Quick Heal is cracked. |
||||||||||||||
Disclaimer: This essay is for EDUCATIONAL purposes
only, if you wish to use the program/game then please BUY IT. |
||||||||||||||
Info: Brand and product names are trademarks or registered trademarks of their respective holders. |
||||||||||||||
Copyright © 1998 by TORN@DO and The Immortal Descendants. All Rights Reserved. |