winxreg.zip - (66k).
winxio.zip - (67k).
Another day, another tutorial, this next program is a very useful tool of our trade with a fairly strong protection scheme, I therefore believe it makes a good program to analyse. Although you will eventually find out that the program can be tricked by manipulating several critical jumps be sure to look further than just the crack.
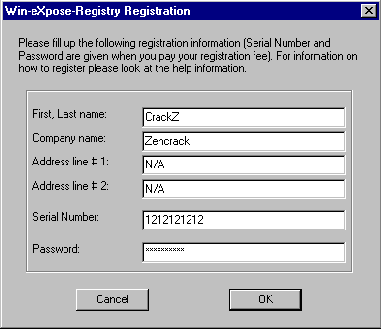
Start the program, you'll locate a registration option in the Help menu and be confronted by the following screen, so lets enter some details in the dialog boxes, (you should enter something in every box to avoid any "did user enter anything" checks), I'll also advise you now that short is best.

For your information the password I've entered is 1313131313. So lets start using SoftICE, with 6 dialog boxes to be copied into memory I advise you use >bpx Hmemcpy and allow the necessary returns (6 in total). Now you could be forgiven for believing that the program checks both the Serial Number: and Password: but this will prove not to be the case, the program will actually work out whether the password is correct with respect to the Serial Number. Lets use SoftICE and trace to this code:
:004023ED MOV EAX,[EBP-1C] <-- Dialog box contents.
:004023F0 PUSH EAX <-- Save on stack.
:004023F1 CALL EDI <-- Gets length of stack save.
:004023F3 ADD ESP,08 <-- Tidy stack.
:004023F6 TEST EAX,EAX
:004023F8 JZ 0040273F <-- Jump_Nothing_Entered.
This code above you'll see several times over, if you've done as I've said you'll
pass all of these checks without a problem. The next section of our code is critical.
:00402448 TEST EBX,EBX
:0040244C JLE 004024B0 <-- Another length check.
:0040244E CALL [006D7B28] <-- Function call and start of loop.
.....
:004024AE JL 0040244E <-- End of loop reached using ESI as a counter.
If your live in SoftICE prepare to be bored, just keep your finger on F10 and watch the loop count variable in ESI until it reaches something close to EBX (it will loop the length of the Serial Number entered). At the end you'll drop out of the JL 0040244E at the most critical routine.
:004024C6 LEA EAX,[EBP-0134] <-- Real password.
:004024CC LEA ECX,[EBP-0234] <-- Password you entered.
:004024D2 MOV DL,[EAX] <-- First letter of good password.
:004D24D4 CMP DL,[ECX] <-- Compare good pwd with yours.
:004D24D6 JNZ 004024F2 <-- Jump_Bad_Password.
:004D24D8 OR DL,DL <-- Good result.
:004D24DA JZ 004024EE
:004D24DC MOV DL,[EAX+01] <-- 2nd letter.
:004D24DF CMP DL,[ECX+01] <-- Check it.
:004D24E2 JNZ 004024F2 <-- Jump_Bad_Password_Again.
:004D24E4 ADD EAX,02 <-- Shift EAX along to next chars.
:004D24E7 ADD ECX,02 <-- Same with ECX.
:004D24EA OR DL,DL <-- Good result.
:004D24EC JNZ 004D24D2 <-- Loop until end of compare.
So the code performs a step by step comparison of your password with the good password, in my case thats f401e1ac, eventually you'll drop out of the loop at the end. Now, you don't actually have to continue tracing, although theres' some pretty interesting looping a little later on, I didn't try this but I would suspect that just fixing the 2 JNZ's so that they never happen (no-opping maybe) would be sufficient.
You should find that the information, along with a KEY is written out to the file wxr95.ini (in the /WINDOWS directory), I've pasted a copy of my example below, note also that this program seems to resist disassembly. You might like to also download Win-eXpose-IO also from the tools page as its system is virtually identical to the one I've discussed here.
[Win-eXpose-Registry 95]
Name=CrackZ
Company=Zencrack
AddrLine1=N/A
AddrLine2=N/A
SerialNumber=1212121212
Key=EXPREF0631BC