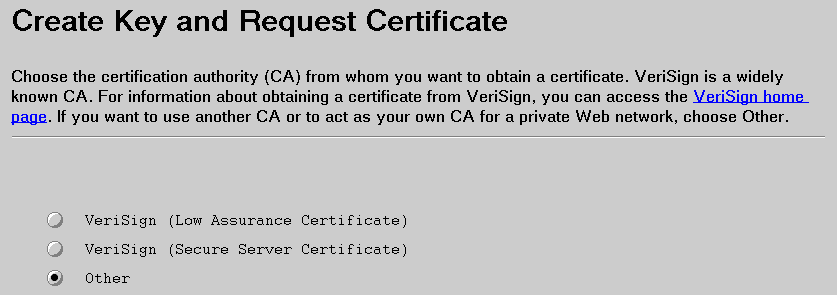
To conduct commercial business on the Internet, you will want to get a secure server certificate from a widely known certification authority (CA), such as VeriSign.
You may, however, have a project for your company, university, or group where you want to act as your own CA for a private Web network. The Internet Connection Secure Server allows you to be your own CA. As a CA, you will use a utility called certutil, which is provided with the Internet Connection Secure Server, to create signed certificates. However, clients must have browsers, such as Secure WebExplorer or Netscape Navigator, that can receive your CA certificate and designate it as a trusted root.
Note: Your use of this utility is limited to directly certifying end user to end user exchange of data. You are not authorized to issue certificates to third parties or allow others to do so, or to use this utility for any other purpose.
This chapter tells you how to become your own CA and then how to process certificate requests as a CA.
Your job as CA is to verify that a certificate should be issued for a client or server. You need to make sure that the person making the request has a legitimate claim to the name in the request. For example, if your company is working on a top secret project, your issuance of a certificate can give a person access to top secret information.
After you have verified a person's claim, you will use the certutil command to process the certificate request. The output from the certutil command is a certificate signed with your CA private key.
After you verify that the information in the certificate created by certutil is correct, you will:
Before you can process certificate requests as a CA, you need to do the following to become a CA:
You must carefully protect your CA private key. If it is compromised, then all the certificates you've issued will also be compromised.
This chapter describes how to use the Create Key and Request Certificate form to create your CA public-private key pair and request your CA certificate.


Specify Key name: Specify a meaningful, unique name to identify your CA key pair. The key name is the label that identifies the key pair and certificate in the key ring. You may use non-alphanumeric characters in key names; however, keep in mind that some platforms have special uses for some of these characters.
Specify Key ring: Specify the fully qualified path and file name for the key ring file. It's best to use a separate key ring to keep your CA key pair. If you specify a file that doesn't exist for key ring, the server creates the file for you.
Specify the Size of the Key Pair: Your private CA key will be used to sign the server and client certificates you process as CA. Your CA public key will be used by those clients and servers to verify your CA signature. The larger the CA key pair, the more secure the key pair will be. If the CA private key is compromised, then all the certificates issued by the CA are also compromised.
The password must be from the U.S. English character set.
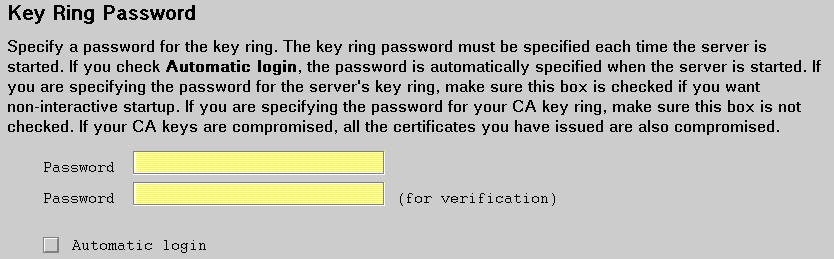
The security of your CA private key, which is used to sign the client and server certificates you process as a CA, depends upon this password. Here are some commonly accepted rules for specifying passwords:
Type the password twice to ensure that you have typed it correctly.
If you must record the password, make sure it is stored in a well-secured place.
If, as recommended, you put your CA key pair on a separate key ring, do not check Automatic Login to stash the password for the CA key ring.

Provide the following information for Distinguished Name:

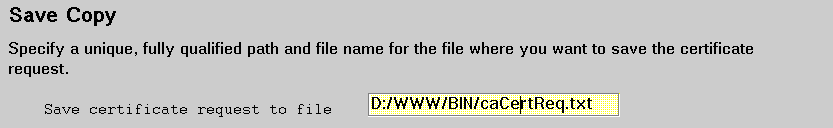
The server:
Use the Receive Certificate form to receive the CA certificate request that you saved. The CA's certificate is the same as the certificate request.

Name of file containing certificate: The fully qualified path and file name of the file in which you saved the CA certificate request (Save certificate request to file on the Create Key and Request Certificate form).
Key ring: The fully qualified path and file name of the key ring you specified on the Create Key and Request Certificate form for your CA certificate.
Key ring password: The password you specified on the Create Key and Request Certificate form for your CA key ring.
The server stores your CA certificate in the CA key ring. It is referenced in the key ring with the key name you specified on the Create Key and Request Certificate form.
You now have your CA certificate (also known as a self-signed certificate) signed with your CA private key in your CA key ring.
Next, the CA key needs to be a trusted root on the server.
Use the Key Management form.
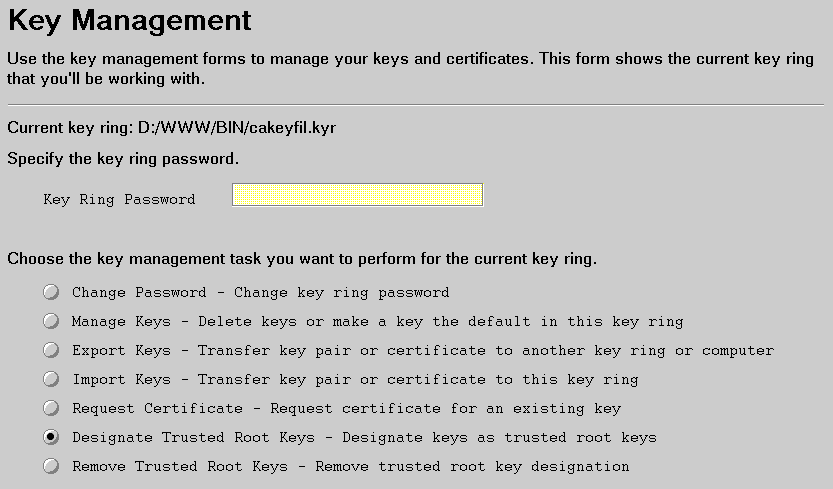

On the Designate Trusted Root Keys form:
Now, you are ready to process the certificate request for clients and servers.
After you have created your CA key pair, obtained your CA certificate, and designated your CA public key as a trusted root, you are ready to act as a CA and process certificates for this server and for other servers and clients.
Servers can use the Configuration and Administration forms to create their public-private key pair and request their certificate. They should use the Other Certificate form. If you provide them with your e-mail address, they can specify it on the form and have the certificate request electronically mailed to you. Or, they can save the certificate request in a file and electronically mail it to you later.
Some browsers, such as Secure WebExplorer and Netscape Navigator, allow clients to create their public-private key pair and request their certificate. Clients can electronically mail their certificate requests to you.
Some e-mail programs may alter files and should not be used to send or receive certificate requests or certificates. For example, some programs may pad the lines of the certificate request or certificate with blanks and invalidate it.
To process certificates for clients and servers, you will:
Then, the client or server can use the certificate you created as a CA to communicate securely with other clients and servers within your private Web network.
Use the certutil command to process certificate requests for the clients and servers for whom you're acting as CA. The output of the certutil command is a client or server certificate that has been signed with your private CA key.
Before using the certutil command, verify that the person making the request has a valid claim to the name in the request.
certutil [-p validity-period] [-k ca-key-ring] < cert-req-file > cert-file-name
certutil -p 730 -k D:/WWW/BIN/cakeyfil.kyr < D:/WWW/BIN/CertReq.txt > D:/WWW/BIN/Cert.txt
Note: The certutil command should be on one line. It is shown on more than one line because of formatting.
After you enter the command, you are prompted for the password of the key ring that has the CA key.
If certutil cannot create the signed certificate, you will get an error message.
It's a good idea to check the output file and verify that the certificate correctly states to whom it is being issued.
What you do next depends on whose certificate you are processing:
If you are processing this server's certificate, you need to:
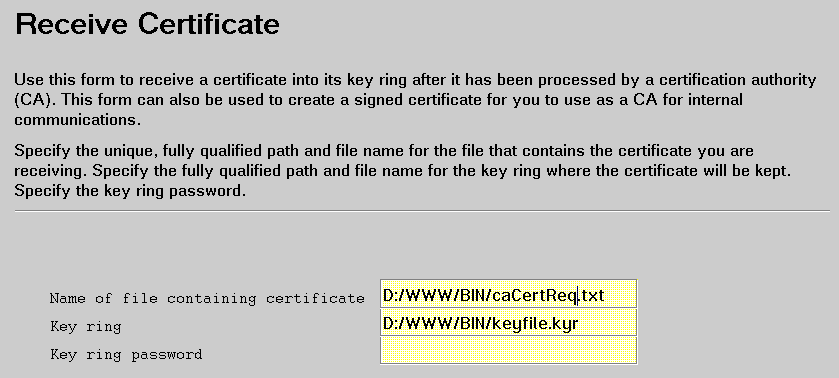
Provide:
The server stores the certificate in its key ring. It is referenced in the key ring with the key name you specified on the Create Key and Request Certificate form for the server's certificate.

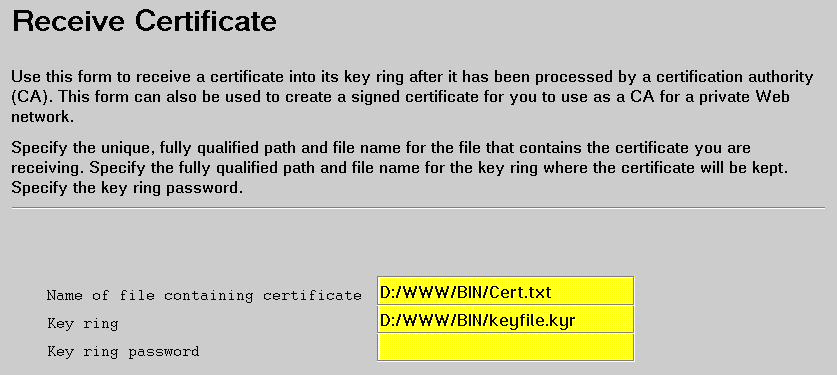
Provide:
The server stores the certificate in its key ring. It is referenced in the key ring with the key name you specified on the Create Key and Request Certificate form for the server's certificate.
After you receive your Confirmation for the Receive Certificate form, you can make changes to other Configuration and Administration forms. However, when you are ready to use the server's keys for secure network communications, you must stop the server and then start it again. The server will not pick up the changes you've made to the key ring if you only restart it.
You need to send the clients and other servers for whom you are acting as CA:
Note: Some e-mail programs may alter files and should not be used to send or receive certificate requests or certificates. For example, some programs may pad the lines of the certificate request or certificate with blanks and invalidate it.
After a client or server receives the CA certificate, designates it as a trusted root, and receives the client or server certificate, the client or server certificate can be used for secure network communications. Before a server's keys are used for secure network communications, the server must be stopped and then started again. The server will not pick up the changes you made to the server's key ring if you only restart it.